Cybercrime is expected to cost the global economy a jaw-dropping $9.5 trillion USD this year. To narrow it down to Salesforce, it’s critical to realize that if misconfigured, more than 150,000 Salesforce-reliant companies, including yours, would be in jeopardy.
In this blog post, we will look at some proven, Salesforce-recommended solutions to guard against potential data leaks. As Marketing Cloud experts ourselves, we know the inside track. So, without any further ado, let’s get started!
1. Apply Salesforce-recommended Security Settings
To begin with, it is important that you follow Salesforce’s security guidelines. Avoid relying solely on your own wisdom while setting up an account.
For instance, some users tend to use the same login information over the years. However, Salesforce recommends frequently resetting your login credentials. You can view the login guidelines in detail here.
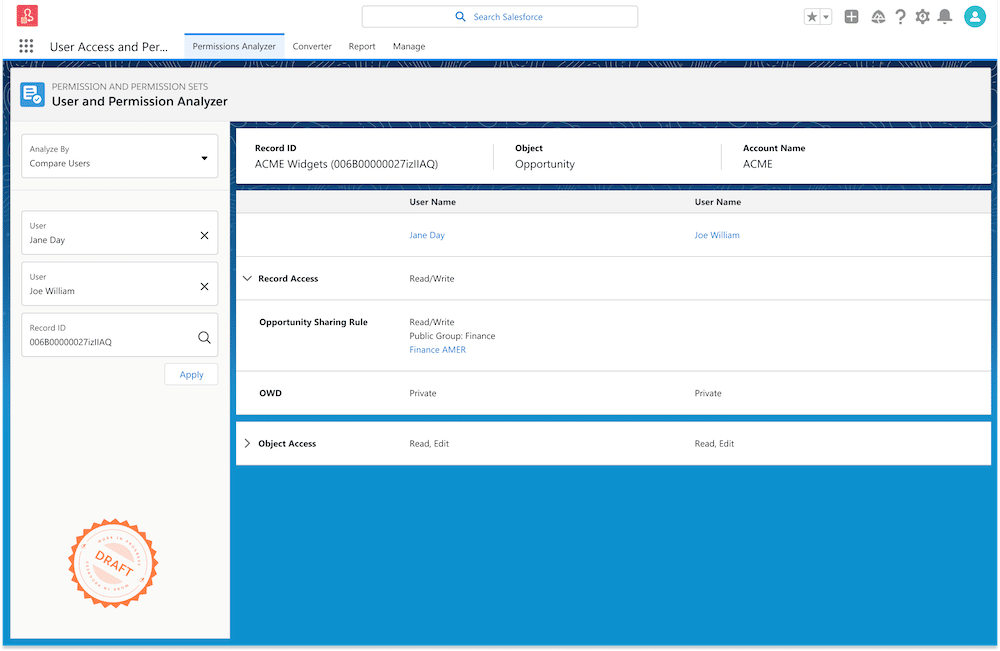
2. Periodically Review Legitimacy of User Access
User management plays an important role in Salesforce security. You need to make sure that users have “the right access to the right data at the right time.”
For instance, if someone has quit your company, they should not be able to access their Marketing Cloud account in the future. Read the full user permissions and access guide here.
You can also try the User Access and Permissions Assistant app, which Salesforce launched in 2022.
“Analyzing, reporting, and managing permissions will become easier for you. You no longer have to export files and do a bunch of calculations on your own to understand a user’s access—the User Access and Permissions Assistant will make these tasks much simpler, ” says Cheryl Feldman, Product Manager at Salesforce.
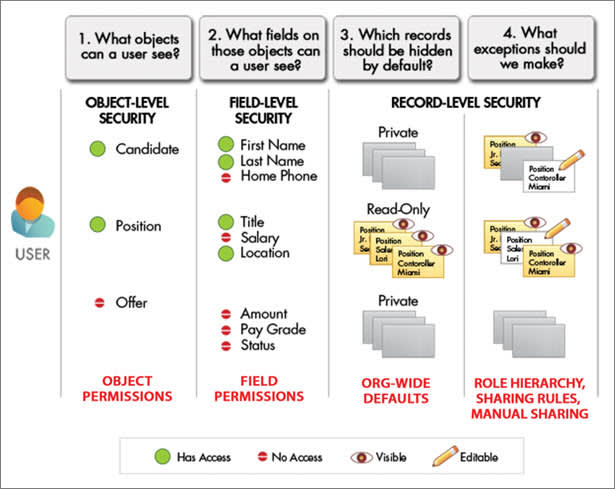
3. Apply The Principle of Least Privilege
Salesforce recommends all admins apply the principle of least privilege, which means granting users only the minimum privilege they need to get their job done. It is a very useful principle for curbing unauthorized access and mitigating security risks.
“A user only has access to specific things (applications, services, etc.) through a predefined pathway, thus preventing a hacker from doing a lot of damage in the event they are even able to gain access to the network,” explains Laura Pelky, Senior Manager at Security Customer Management, Salesforce.
4. Disable The API User Checkbox
Unless you are an integration user, you don’t need to enable the API User checkbox in the setup process.
We mentioned how important it is to reset login credentials from time to time. However, passwords for API users do not expire. Therefore, we recommend using the OAuth protocol as it provides a more secure authentication flow. You can read more about how to implement authorization to grant safe access to REST API resources here.
5. Prevent API Credential Exposure
In order for your API integration to access Marketing Cloud, you need to assign it “scopes” in Installed Packages. Now, what is a scope? A scope may be defined as a library of permissions and behaviors in the Marketing Cloud.
Instead of enabling all options in the scope, you want to choose a select few according to the level of authorized access available. Why? Because in the event of a potential credential exposure, bad actors can perform any user action without having to log in to Salesforce.
Equally, you need to consider where and how you store your API credentials. Feel free to learn more about credential exposure right here.
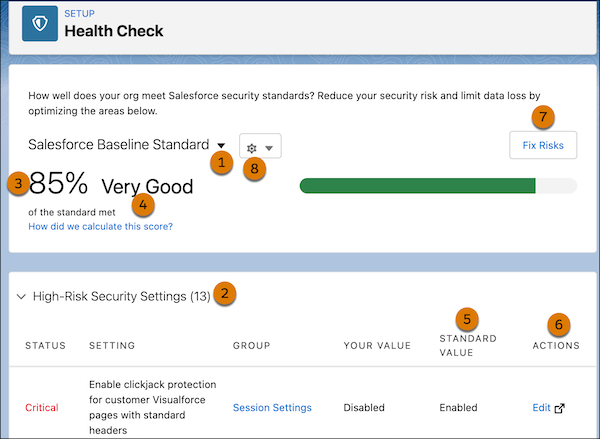
6. Utilize Salesforce’s Native Health Check Feature
Health Check is a free tool that enables Salesforce admins to review the security status of their organization. This feature provides a very comprehensive view of your org security.
Health Check has a native security baseline called the Salesforce Baseline Standard. You can also add up to five custom standards if the native baseline does not align with the peculiar needs of your business.
To give an instance of how Health Check identifies risks: imagine you changed the length of your password and made it shorter than the recommended length. The tool will list this setting as a potential risk since length is the most critical aspect of a good password.
7. Use Salesforce Authenticator
Salesforce Authenticator is a mobile two-factor authentication app. It’s a simple, highly effective security solution for businesses whereby employees can approve/deny logins with a single tap on their mobile devices.
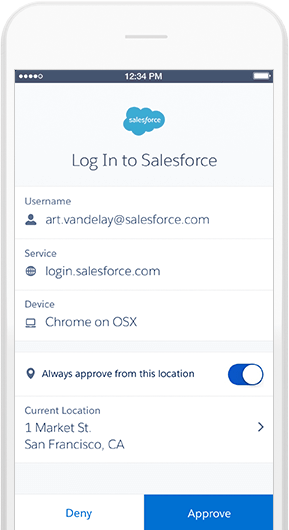
Image Source
You can also use Lightning Login to access your account without needing to type your password. You just need to enter your username and approve the login with Salesforce Authenticator and your thumbprint.
Lightning Login eliminates the need to remember passwords, which are often the weakest bolts in the security apparatus.
8. Enable Multi-Factor Authentication
Multi-factor authentication (MFA) provides an “extra layer of protection” against security breaches such as credential stuffing, phishing, and even account takeovers.
At its simplest, “multi-factor” means that any potential attacker needs to overcome multiple obstacles to enter the Salesforce ecosystem.
So it’s no longer just about the username and password, which attackers can quickly breach. Salesforce has provided a detailed multi-factor authentication guide for admins where you can learn more about how to implement MFA in Salesforce.
9. Establish A Secure Connection
Salesforce recommends using a virtual private network (VPN) to enhance the security of your internet connection. Alternatively, you can also enable encryption by using a router’s administrator console. Follow these steps to access a router as an administrator:
- First, you need to identify the IP address of the router.
- Visit your preferred browser and request a connection to the router by entering the router’s IP address in the address bar.
- Enter the admin login credentials and access the settings.
Before proceeding, make sure you are connected to the right router. You can learn more about how to safeguard your internet connection on this dedicated module.
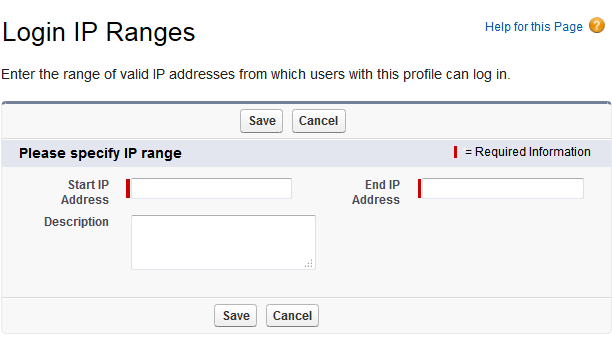
10. Restrict Access by Setting Login Ranges
By defining a specific range of trusted IP addresses, you can restrict foreign access to Salesforce. As a result, each time a non-trusted IP seeks to gain entry, it must verify its identity. You can also restrict login hours by setting up a custom schedule.
Learn how to set login ranges on this Trailhead module.
11. Take Device Security Seriously
In cases where employees have lost their devices, a data breach is a very immediate threat. Therefore, ensuring device security is of the utmost importance.
You can secure your mobile/laptop by taking basic security measures. Start by creating a long, unguessable password for your device. Make sure to scan all files with antivirus software before accessing them. You may also want to encrypt your hard drive. Try using VPN while working on Salesforce. Lastly, avoid keeping your device lying around here and there.
Wrapping Up!
The list is by no means exhaustive. Data security is complex. It has many layers. In our post, we highlighted the most important starting points when it comes to Salesforce security.
Our recommendation would be to review all Salesforce resources related to security. In the event of a data breach, you don’t want to be surprised. Cybercrime is an ever-increasing threat, and notwithstanding the robust security measures baked into the platform, it is important to be on your guard at all times.


Mrugesh Dabhi
Latest posts by Mrugesh Dabhi (see all)
Grow Your Subscribers Effortlessly: Learning to Curate the Perfect Email Capture Landing Page!
Top Pardot Features That Will Help You Ace Your Marketing Automation Game!