Content
- Phishing Email Examples
- What is Phishing?
- Phishing and Social Engineering
- The Origins of Phishing
- Phishing Statistics That Every Organization Should Know About
- Types of Phishing
- Types of Evolving Phishing Scams
- Phishing-as-a-Service and Phishing Kits
- How to Recognize a Phishing Email
- Impact of Phishing Scams
- How to Stop Phishing Emails
- Conclusion
In November 2014, Sony Pictures Entertainment was the target of a spear phishing attack. Numerous employees – including CEO Michael Lynton – received emails urging them to verify their Apple IDs because of purported “unauthorized activity”. These “phishing emails” looked very real, but actually came from hackers who posed as company colleagues to fool the victims into clicking on links included in the message. By doing this, they ended up on a malicious site that prompted them to enter their Apple ID information. The hackers then used these credentials to launch malware that crippled Sony’s computer networks, and allowed the attackers to steal over 100s of GB of proprietary data including emails, financial reports, and digital copies of newly-released films.
In email phishing attacks, the attackers’ goal is almost always to get the victim into providing some sensitive information, such as login credentials, and then use this information to impersonate the victim, perpetrate identity theft, or steal more data or money. Phishing attacks are a common and dangerous problem for organizations all over the world – and this guide will explain why.
This detailed guide answers many common questions about email phishing, including:
- What is email phishing?
- How does it work?
- What does a phishing email look like?
- What are the different kinds of email phishing attacks?
This resource is both informative and action-oriented, so you can also understand critical issues like:
- How to spot email phishing
- How to report email phishing
- Tips for email phishing prevention and email phishing protection
Phishing Email Examples
The Sony incident is just one of many high-profile email phishing examples from the past few decades.
Google and Facebook
Between 2013 and 2015, Google and Facebook were the targets of a Business Email Compromise (BEC) phishing campaign, in which the attacker fooled both companies into paying fake invoices. Although the scam was eventually discovered and the perpetrator sentenced to jail time, he ended up costing the two tech giants over $100 million.
Ledger
One of the most recent and well-known phishing email examples is from December 2020.
Ledger makes hardware cryptocurrency wallets to store users’ private keys offline and protect their crypto assets. Scammers sent phishing emails to thousands of users to get them to download a fake version of the Ledger Live app and enter their 24-word recovery phrase. This allowed the attackers to access and steal the users’ cryptocurrencies. Through this campaign, they eventually stole and exposed 272,000 customer names, mailing addresses and phone numbers, leaving all these customers vulnerable to data, financial, and identity theft.
The Nigerian Prince Scam
Almost every email user – that’s over 4 billion people – has received an email from a “Nigerian Prince”. Also known as a Nigerian letter scam, these phishing campaigns start with an email from a foreigner who claims to be royalty with a “wonderful new investment opportunity”. They ask the potential victim for their bank account number in order to send them a huge amount of money in return for a small advance payment to cover the expense of international money transfer. If the recipient falls for the claim, the Nigerian Prince takes the payment from the person or, worse, drains their bank account.
In 2018, Americans lost $703,000 last year to such frauds. These scams are still highly effective because they play on two key human vulnerabilities: greed and lack of awareness. Sometimes, scammers prey on victims’ desire to help a person in need.
The Nigerian Prince fraud is one of the longest-running Internet frauds, not to mention the best-known example of an email phishing attack.
What is Phishing?
Phishing is a type of cyber attack in which the attacker uses disguised email as a weapon. Although phishing attacks are sometimes carried out via telephone (voice phishing or vishing) or through text messages (smishing), a majority – 96% to be precise – are delivered via email. Further, research suggests that in 2020, 1 in every 4,200 emails was a phishing email.
In a phishing scam, a target recipient (or recipients) receive an email from a scammer impersonating a legitimate sender, such as a:
- Bank
- Other kind of financial organization, e.g. an insurance company or mortgage provider
- Some other well-known company
- University
- Government agency or department, e.g. the income tax, social security, unemployment benefits, etc.
Often, the email includes a link that looks like a genuine website belonging to the legitimate sender, but is actually malicious and fully controlled by the scammer. The attacker then encourages the victim to click on the link and enter their sensitive data, such as:-
- Personally Identifiable Information (PII): Name, address, phone number, email address, social security number, etc.
- Banking details: Account number and login credentials
- Credit card details: Card numbers, PINs and CVV codes
- Login credentials to sensitive or private online accounts
In many cases, the purpose of a phishing campaign is to auto-install malware or ransomware on the victim’s computer. Once the ransomware is installed, it allows the attacker to lock the device, so the user can’t access their files or data. To unlock these assets, the scammer demands a ransom from the victim.
Phishing emails are often well-designed and cleverly disguised to spoof legitimate organizations, so recipients are fooled into trusting both the email content and sender. Since victims fail to pick up on common ”red flags”, they click on malicious links or download malicious attachments in the email, and end up sharing sensitive information with or losing money to the scammer.
Phishing and Social Engineering
Phishing is one of the most common forms of social engineering, which refers to malicious activities that use psychological or social manipulation by instilling fear, anxiety, panic or curiosity in victims. Through phishing attacks, the attacker tries to trick a victim into:
- Making security mistakes that allow the hacker to access the victim’s system or other systems on the enterprise network
- Giving away sensitive information, e.g company secrets, blueprints or financial data
- Clicking on links to malicious websites to reveal sensitive credentials
- Opening malicious attachments to install ransomware or other malware on the victim’s device
Often, attackers design their phishing emails to:
- Spin a false story (the Nigerian Prince scam is one example)
- Create a sense of urgency to push the victim into making a decision
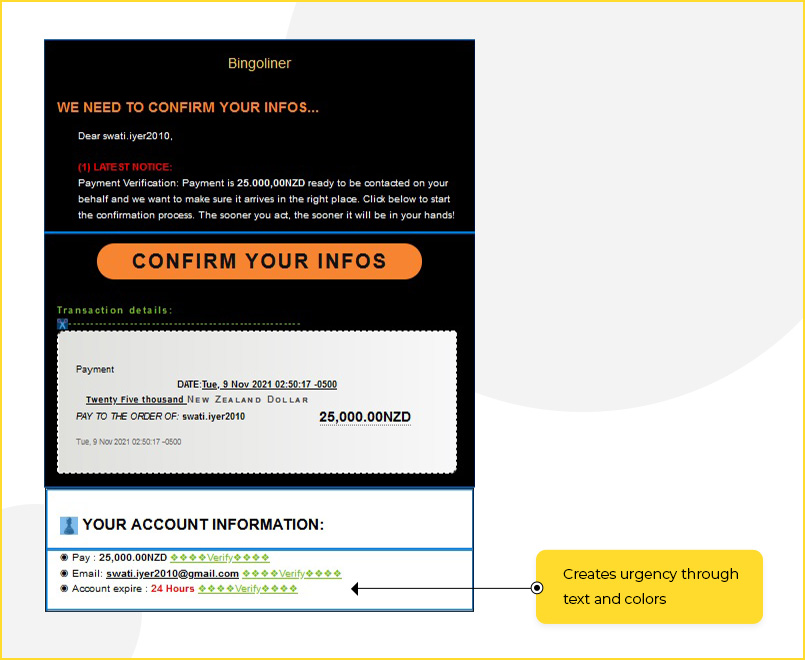
- Make false promises about wealth, product offers, free holidays, etc.
- Intimidate or scare the victim into compliance
Such attacks are especially dangerous because they rely on human errors, vulnerabilities and unpredictabilities, rather than on security weaknesses in devices, networks, software or operating systems. This is why phishing remains a huge problem all over the world.
The Origins of Phishing
Phishing scams have been around since the early 90s, when they were first sent to AOL users. The first recorded mention of the term “phishing” is also connected to AOL within a Usenet newsgroup called AOHell, an AOL for Windows add-on. This program was designed – allegedly on the basis of advice from a disgruntled AOL ex-employee – to steal the passwords and credit card information of legitimate users.
In this scam, the phishers sent bulk fake emails, and fooled recipients into clicking on fake sites and entering sensitive information that the scammers then used to steal money from victims. These phishing techniques are used by scammers to this day. Nonetheless, phishing has evolved into a more sophisticated crime since those early days. It has also grown into a massive industry, costing large U.S. companies an average of $14.8 million annually, almost 3.5X the 2015 cost of $3.8 million.
Further, many of today’s email phishing scams:
- Are automated, allowing for easy bulk sends
- Contain engaging subject lines that encourage recipients to open them rather than ignore them (as they should)
- Almost perfectly impersonate genuine emails from trusted sources to fool recipients into downloading malicious attachments or click on malicious links
Also, modern phishers often send out a small number of dodgy emails targeted at specific users. They can thus avoid detection by email spam filters, and increase their chances of getting recipients to fall for the scam.
The world’s first-ever phishing lawsuit was filed in 2004 by the U.S. Federal Trade Commission. Since then, phishing-related lawsuits have become common, although the threat of legal action does not always deter potential phishing scammers. The next section will explain why.
Phishing Statistics That Every Organization Should Know About
In 2020, phishing was the top “action variety” in breaches, and 43% of breaches involved phishing and/or pretexting. The FBI also says that in 2020, phishing was the most common type of cybercrime, and phishing incidents nearly doubled in frequency between 2019 and 2020. Phishing attacks against organizations are now so common that in 2020:
Worldwide, businesses lose $17,700 every minute due to phishing attacks. Moreover, phishing is the second most expensive cause of data breaches, costing organizations an average of $4.65 million.
A BEC attack in which attackers hijack or spoof a legitimate corporate email account ranks as the #1 most expensive cause of data breaches, with a single attack costing businesses $5.01 million on average. But short-term costs are not the only problem that organizations have to deal with in the aftermath of a phishing attack and breach. According to Verizon, companies also experience a 5% drop in stock price in the 6 months immediately after a breach.
U.S. organizations are particularly attractive phishing targets. 74% of them experienced a successful phishing attack in 2020, 14% higher than 2019, and 30% higher than the global average. Nonetheless, many companies in other countries also experienced successful phishing attacks:
- United Kingdom: 66%
- Australia: 60%
- Japan: 56%
- Spain: 51%
- France: 48%
- Germany: 47%
Phishing has become especially common with the increasing prevalence of phishing websites. By January 2021, Google Safe Browsing had registered 2 million+ phishing sites, a 27% jump over January 2020, and discovered that there were 75X as many phishing sites as there were malware sites.
As the examples in the introduction show, no industry is safe from email phishing attacks:
- Japan’s Sony is a media company
- Facebook and Google are both technology organizations
- Austria’s FACC is an aerospace parts maker
- Belgium’s Crelan Bank is a financial services firm
- MacEwan University is an educational institution
However, some industries seem to be more vulnerable to phishing than others. According to Statista, in Q1 2021, the sectors that were most frequently targeted are:
- Financial institutions: 25%
- Social media companies: 23.6%
- SaaS companies: 19.6%
- Payments processors: 8.5%
- Ecommerce or retail companies: 7.6%
According to other research, these industries are also at risk of email phishing attacks:
- Healthcare and pharmaceuticals
- Technology
- Manufacturing
- Construction
- Business Services
- Education
In 2020 and 2021, healthcare has been hit particularly hard by phishing. Between August 2020 and July 2021, U.S. healthcare providers were hit by 58.8 of data breaches on average, with around 3.70 million healthcare records breached per month. Many of these breaches were caused by phishing, either directly or indirectly.
Types of Phishing
The most common types of phishing scams are:
Spear Phishing
In this targeted attack, the scammer crafts an email targeting a specific individual or group. The attacker first identifies the target, and then uses spoofed email addresses to send messages that look as though they’re from genuine entities, such as organizations or co-workers. For instance, the attacker may pretend to be a manager and email a specific employee urgently requesting a large bank transfer.
Whale Phishing or Whaling
This attack targets senior leaders like CEOs or board members. The scammer tricks the victim with a fake email to get access to their login credentials in order to steal enterprise data or set up an Advanced Persistent Threat (APT).
CEO Fraud
The hacker impersonates the CEO or some other high-ranking official, and emails an employee authorized to access or pay out money, such as a member of the Accounts Payable team. The attacker requests the employee to provide sensitive information or asks them to transfer funds to a bank account. The email appears to come from the CEO, so the employee usually complies immediately.
Clone Phishing
The attacker creates a replica of a legitimate message that the victim may have already received. They send the fake message from an address resembling the legitimate sender’s address, and also replace any original links or attachments with malicious links or attachments. In such attacks, there is often a sense of urgency to scare the victim into clicking the link or opening the attachment.
Snowshoeing
Snowshoeing is a type of “hit-and-run spam” attack wherein the spammer sends messages via multiple domains and IP addresses to spread large-scale misinformation or panic.
Types of Evolving Phishing Scams
Over the past few decades, many other types of phishing scams have evolved. These include:
Polymorphic Phishing Scams
The scammer makes a small or random change to an email’s subject line, sender name or domain, which allows the email to escape traditional signature-based email defense solutions, or automated link-scanning programs.
Hijacked Search Results
Phishers hide their malicious fake sites behind legitimate or benign sites. They then send emails containing legitimate URLs which then redirect the victim to a phishing page. Since the link appears to be genuine, victims are more likely to click on them, and get fooled.
HTTPS Sites
HTTPS sites were used by 74% of phishing scams in Q4 2020. Scammers create spoofed websites with the lock icon in the browser address bar (hence HTTPS), fooling victims into thinking that the email is from a trusted source.
Dynamic Phishing
Dynamic phishing leverages an attacker-controlled server. Scammers send out emails with URLs pointing to this malicious server, which captures company-specific information like its logo and banners to look real, and fool victims into parting with information or money.
Phishing-as-a-Service and Phishing Kits
With the availability of Phishing-as-a-Service” (PhaaS) and phishing kits, the phishing landscape has evolved into a thriving service-based economy. Much like Ransomware-as-a-Service (RaaS), PhaaS is helping to commoditize phishing, and contributing to its increasing ubiquity and danger. PhaaS follows the subscription-based SaaS model, wherein attackers pay an operator to develop and deploy phishing campaigns.
Attackers can also purchase affordable phishing kits on the Dark Web, which contain almost everything they need to design a phishing campaign, including:
- Evasion mechanisms: E.g. HTML character encoding
- Website development software
- Email templates
- Sample scripts
- Automated malware distribution software
- Victim email addresses
Both phishing kits and PhaaS enable scammers to create successful phishing scams with very little effort.
How to Recognize a Phishing Email
Let’s start by understanding what a phishing email looks like.
A well-designed, cleverly-disguised phishing email looks like a genuine email from a legitimate organization. The scammer impersonates a genuine entity that the victim would normally trust, such as a company or government institution. Clever impersonation is one of the key success factors of an email phishing campaign, and it happens in the form of the:
- Sender’s name in the sender’s email address and signature
- Genuine-looking domain name in the sender’s email address
- Logo in the email body
- Company name in the email subject, body, and sender’s signature
The email text tries to trick the victim into believing that the message contains something they want or need. This could be a:
- Request from their bank to update their account details
- Request from a company supervisor or senior leader (e.g. a CEO) to send money to a specific bank account
- Free holiday or other kind of lucrative “too good to be missed” offer, such as free bitcoins
- An urgent message from a government department that scares the user into doing something urgently. E.g. “Change your password within 1 hour or your funds will be frozen.”
Almost always, a phishing email contains a link to a website that looks genuine, but is actually malicious and controlled by the attacker. The scammer urges the recipient to click on the link. Once the fake website opens, the victim is asked to enter some sensitive information, e.g login credentials, credit card numbers, social security numbers, etc. The email may also contain a malicious attachment, which when opened infects the victim’s computer with dangerous malware or ransomware.
Next, let’s look at the red flags that can help differentiate phishing emails from genuine emails.
1. Email Body
- The logo’s design, placement, colors, etc. look a little different
- The text contains grammatical or spelling mistakes
- The formatting is inconsistent or generally poor with glaring misalignment issues
- The greeting is generic or completely missing
- The message creates a sense of fear, urgency or panic
- Contains banners that don’t seem to belong to the brand, or don’t match the email purpose
- Unexpected attachments that are either unrelated to the email message, or contain a possibly dangerous file type, e.g .iso, .exe, .jar, .cmd, .reg, etc.
2. Malicious Link and Fake Website
As mentioned earlier, almost all phishing emails include suspicious links. It is possible to identify if a link is suspicious or not by identifying these red flags:
- The URL doesn’t match the email’s context. E.g. a message from “FBI” contains a link that takes the user to: http://interweb30.fbi.com/membershipkey=00000
- The domain portion is obscured or confusing, so the user sees something like http://fbi.replica.com
- The site throws up an unexpected “security certificate expired” message
3. Missing HTTPS
Genuine websites, especially websites where financial or other kinds of sensitive transactions take place, always include HTTPS in the URL. Web browsers show a lock icon for HTTPS pages, indicating that they’re safe to use. However, fake phishing websites use HTTP instead of HTTPS. This is an obvious red flag that this website supposedly belonging to “Bank of Timbuktu” is actually fake.
Mis-spelled organization names in the URL are another red flag. For example: https://www.microsift.com, instead of https://www.microsoft.com.
Moreover, in a phishing website, the URL’s Top Level Domain (TLD) would also look different with added characters or numbers that should not be there. For example, if the site shows http://f45619.shopify.ae instead of https://www.shopify.com – it’s fake.
4. From, To, and Subject
- The sender is not someone the recipient normally communicates with, or expects to receive an email from
- The sender’s email address includes a public email domain like gmail.com, even though it is purportedly from a legitimate organization
- Or it is from a suspicious domain, e.g. hp-awesomesupport.com
- The domain name is spelled incorrectly but the difference is not obvious, e.g. sarah@hrnedical.ae.pk instead of sarah@hrmedical.com
- The genuine company’s name in the email address contains strange characters, such as numbers or special characters like $, #, &, etc.
- The email is sent to an unusual mix of people, e.g. those whose last names start with the same letter
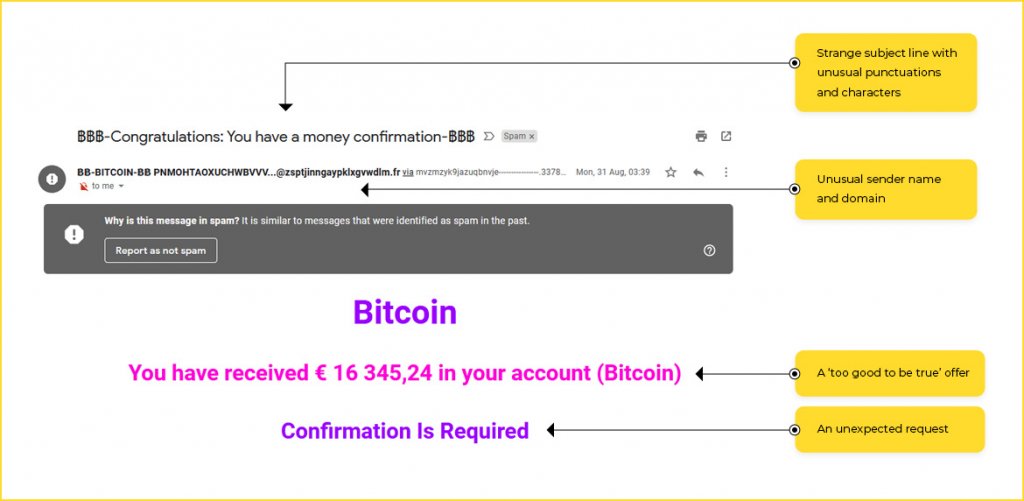
- The subject line is irrelevant or does not match the message content. It may also look unprofessional with casual language, or too many special characters, punctuation marks, or emojis
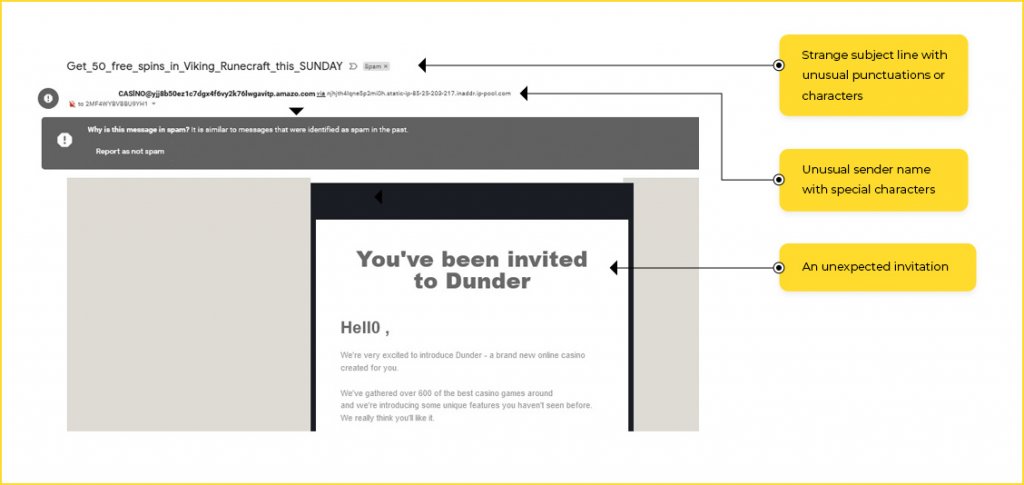
So how to spot email phishing? Here are some ways:
Look out for obvious red flags:
- Inconsistent formatting and spacing
- Non-standard fonts
- Logos that look different from the company’s standard logo (it’s easy to verify this on the company’s official website)
- Text, banners, or images that look out of place
- Too good to be true offers that promise a huge payout in return for a small amount of money
Check the email and email address:
- Spelling or grammatical errors
- Unprofessional language in the subject line and/or body
- Comes from a public email service provider, e.g. johnfromamazon@gmail.com
- Incorrectly-spelled company name in the sender’s address, logo or signature, e.g. Hubsoft instead of Hubspot
- Address contains additional characters instead of a professional name, e.g. john1l0veY0u@facebook.com
- Includes text and link to take urgent action “or else”
- Unexpected attachments
Keep an eye out for these common subject lines (or their variations) that usually indicate a phishing email:
- Re:
- Congratulations: You have a money confirmation
- Hey Dear!! You’re one of the lucky ones!
- De-activation in process
- You have a new voicemail
- Request to withdraw payment is approved
- Meet local beauties
- You have received $$ to your account
- Lose 30 lbs in just 2 weeks
- Your order with abc.com
- Failed delivery for package #12456
- A friend tagged a photo of you
Check the browser URL both in the email and in the browser window. The site is most likely fake if it:
- Contains strange characters
- The main domain name is mis-spelled
- The main domain name includes other words or character strings like “X712Ls” or “replica.apple.com”
- Starts with HTTP instead of HTTPS
- Does not display the lock icon
Impact of Phishing Scams
Phishing scams have become extremely common, which is why there were almost 12X more phishing complaints in 2020 compared to 2016. At an organizational level, phishing campaigns are usually directed at more than one person, and the expected payouts are also larger. According to research, after a phishing attack, 60% of organizations lost data, 52% experienced credential or account compromise, and 47% were infected with ransomware. Further, it only takes one mistake by one employee to subject the entire organization to:

However, organizations can take actions to both spot and stop phishing emails to protect their assets, data, and people. These strategies are covered in the next section.
How to Stop Phishing Emails
Strong Security Controls
First, email phishing prevention starts with strong security controls such as:
- Updated antivirus, anti-malware, web filters and firewalls
- Secure email gateways with anti-spam, anti-malware and policy-based filtering
- Modern web browsers with built-in protection against phishing sites
- Regularly patched and updated software
- Strong password policies plus password managers to safely and securely store encrypted passwords, and prevent the possibility of compromise
- Network-level anomaly detection for inbound and outbound emails
- Two-factor or multi-factor authentication to prevent account takeovers via phishing scams
Advanced Threat Protection (ATP)
Phishing scams have evolved so scammers can now design campaigns that are not caught by traditional security solutions. However, ATP solutions can expose modern-day, sophisticated phishing scams, even if the emails are hidden behind legitimate domains or services, or contain multiple layers of redirectors.
Robust ATP solutions are Machine Learning-enabled, and can identify phishing sites and scams in real time. Moreover, they learn from scams, and improve their ability to provide stronger, more reliable protection against many types of phishing attacks.
Deploy Proactive Phishing Prevention Tools
“Ahead-of-threat” attack prevention tools can reduce the probability of phishing attacks. This approach involves monitoring and analyzing Domain Name Server (DNS) traffic and data to:
- Identify and block malicious domain names used to register malicious phishing websites
- Detect and isolate infected devices or endpoints to minimize damage across the network
Some solutions provide actionable information to support forensic investigations after a phishing attack. Organizations can further prevent phishing attacks from spreading across the enterprise network by deploying strong Endpoint Detection and Response (EDR) tools.
AI-based tools can also help detect and prevent potential phishing attacks. Such tools learn users’ email communication habits, automatically detect anomalous or suspicious behaviors, scan inbound links in real time, and provide security teams with actionable data to respond to attacks. These tools go beyond simple signature detection to proactively fight phishing inside users’ inboxes.
Simulate Phishing Attacks
Simulated phishing attack tests are a good way to test phishing awareness within the organization. Also known as phishing penetration tests, such tests enable security teams to take remedial action to train users, build a strong email security awareness program, and improve the organization’s ability to fight the phishing menace.
For maximum effectively, phishing penetration tests must:
- Be conducted regularly
- Mimic real-life phishing attacks with emails that result in users submitting sensitive information on a fake website
- Monitor which fake emails are opened or clicked, and have credentials entered
Other Strategies for Email Phishing Protection
Organizations should also implement the following strategies to minimize the impact of phishing attacks:
- Regularly monitor the status of all software and equipment with SIEM, EDR and penetration testing
- Use strong encryption for VPN and other remote access tools
- Schedule regular, automated data backups
- Train employees at all levels on:
- What is phishing
- Why is phishing so dangerous
- How to spot email phishing by identifying red flags
- How to flag emails correctly
- How to report phishing emails to:
The immediate supervisor
The IT department
Public safety organizations such as the:
# Police
# the Anti-Phishing Working Group at reportphishing@apwg.org (U.S only)
# The FTC at ftc.gov/complaint (U.S only)
Conclusion
Phishing is one of the most ubiquitous and dangerous threats to businesses. Following a successful attack, an organization could lose vast sums of money or sensitive/business-critical data. This can affect its compliance posture, increase customer churn, and affect its reputation. Often, such attacks result in attackers gaining access to vital business systems, or persisting within the enterprise network to launch other kinds of cyber attacks.
For all these reasons, it’s vital for organizations to increase their awareness of email phishing, how to spot email phishing, as well as email phishing prevention, and how to stop phishing emails. We hope you found this guide useful. Feel free to download, print it or share it with others!
A great way to avoid phishing attacks is to work with email experts who understand your business, and can recommend tailored anti-phishing strategies. For help in this area, contact the Email Uplers team.





Kevin George
Latest posts by Kevin George (see all)
Take Interactivity to the Next Level with Kinetic Email Design
Email Retargeting - A Quick Guide To Get Started